Protect Your Computer Files Against the CryptoLocker Virus with External Backup
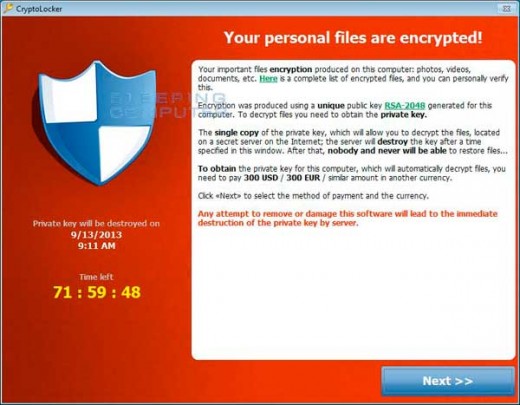
The Dreaded CrypoLocker Payment Screen
Oh, no! Not Another Computer Virus!
Recently I've read several news reports from reputable sources about a new computer virus that's spreading like a California wildfire. Its name? CryptoLocker--a virus with the potential to destroy all your computer files, and it's rapidly taking hostages.
Hostages? Did you read that right? Yes, you did. CryptoLocker is a type of ransomware, and "ransom" is the operative word. When the virus invades a computer and infects its system, key files on the hard drive are encrypted and made inaccessible to the user. They are held hostage for a ransom.
Your security software or a computer expert may be able to "uninfect" your computer, but neither can unlock those encrypted key files or allow you access to your computer. Security software companies haven't been able to produce a protection against this virus yet. Even an expert computer tech won't be able to rescue your encrypted files from CryptoLocker. No one but the hackers responsible for the virus can do that--and they have a price. A box on your computer screen will tell you the amount of the ransom and how many hours you have to pay it--usually $300 within 72 hours, although there are accounts of some $700 ransom demands--and the countdown begins on the screen.
So far (and I'll update this if I learn otherwise), this virus is only affecting Windows on PCs. But people with Macs shouldn't start feeling complacent. Successful hackers may decide to diversity.
Scammers are already trying to get in on the act and make some money from this virus scare. When searching "cryptolocker", I saw a link "promising" an "easy trick" to unlock files. Don't be taken in by such false promises. In addition, some copycat hackers are putting messages on computer warning your computer is infected even when it isn't. What's a person to do?
http://commons.wikimedia.org/wiki/File%3ABitcoin.png

Should You Pay the Ransom?
Only you can decide if your computer files are valuable enough for you to allow yourself to become the victim of extortionists. If you don't regularly back up your files--and this is important--even if you regularly back up your files to an external device, but you leave that device connected to your computer all the time (as many people do), or if it just happens to be connected at the time CryptoLocker attacks, you may not be able to recover them.
In addition, all the files in shared network files connected at the time of a CryptoLocker invasion may also become encrypted.
Some security experts say this is the worst computer virus they've ever seen. They warn that the cryptography algorithms used by the CryptoLocker virus were developed as long as 30 years ago by governments, even the military, and are unbreakable without the key.
There's the rub. The criminals behind this destructive virus have the key. They also have an evil plan--to force you to pay for the decryption of your files. If you have years of family photos stored online without external backup, or if you have in-process or completed work files stored on the same computer that you use to access email and the Internet, or if you have multiple computers connected via a network, you may have no alternative but to pay up in order to retrieve data and/or images you don't want to lose.
If you choose not to pay by the deadline, the hackers show no mercy. They follow through with their threat and destroy your files. ZAP!
So far, the crooks have kept their promise to decrypt files once they received ramsom payments via hard-to-trace methods as Bitcoins and Green Dot Moneypaks. Does this mean there's some honor among thieves? Not necessarily. Once they've held you up for ransom and you've given them the currency they demanded, who's to say they won't do it to you again?
An estimated 3% of victims paid to rescue their files as of mid-October, 2013, validating the hackers' theory that they launched a profitable business. This means they'll keep on infecting PCs, demanding ransom and destroying files when it's not paid. In short, they'll continue to act as all successful extortionists do.
Back up Your Computer Files Externally--NOW!
If you don't have an external backup device of any type, you should get one ASAP. It's a good investment when you consider the alternative. Most people have one or more flash drives around, but the newer model external storage hard drives are not only faster, but much less expensive than they used to be. You can get a 1TB (that's 1,024 gigabytes) external drive that connects to either a 2.0 or 3.0 USB port. The 3.0 is about three times faster, especially with very large files. Western Digital and Seagate both have 1TB external drives that retail for less than $100. Are your precious photos and manuscripts-in-progress worth it? You bet! In fact, you should have at least two external backup devices and not keep them stored in the same place (in case of fire or other hazards).
~~~~~~~~~~~~~~~~~~~~~~~~~~~~
CryptoLocker gains access to a computer via driveby downloads (read about them here: http://en.wikipedia.org/wiki/Drive-by_download) or infectious attachments to emails (bots) masquerading as legit business emails. Emails purported to be tracking notices from UPS or FedEx may actually be fakes providing a path into your computer's hard drive.
Now is the time to be extra vigilant about the sites you visit on the Internet, downloading from the Web, as well as double-checking the safety of all emails and social network messages before opening. If in doubt, don't do it. Delete suspicious emails unopened.
I encourage you to visit the IT Leaders CryptoLocker Ransomeware Information Guide and FAC (URL shown below) and print all seven pages "just in case." It was compiled on October 14, 2013 and updated October 16. It probably has the most accurate and thorough information extant about CryptoLocker. Its focus is on helping the users of infected computers.
As writers, we work hard to put our words down. Most of us do it on-screen in Word documents, especially early drafts, and many writers don't copy their early work onto a disc or flash drive at that stage. Even if you have a very good memory, you probably don't want to reconstruct an article or story from the recesses of your mind. With this devious virus, CrytoLocker, on the loose, you may want to save even those snippets of writing externally to ensure they're preserved. As with viruses that infect humans, the bottom line is prevention. Routinely backing up your important files is the best thing you can do to keep them safe.
Hopefully, the good guys (and gals) will catch the bad ones--the hacker/extortionists--and put an end to CryptoLocker for good!
Would You Pay the CryptoLocker Ransom?
If your computer or computer network contains important files (documents, images, spreadsheets) that aren't backed up, would you pay a ransom to rescue them if CryptoLocker encryped those files?
Protect Your Computer Files

CryptoLocker--Begone!
As writers, we work hard to put our words down. Most of us do it on-screen in Word documents, especially early drafts, and many writers don't copy their early work onto a disc or flash drive at that stage. Even if you have a very good memory, you probably don't want to reconstruct an article or story from your mind. With this devious virus, CrytoLocker, on the loose, you may want to save even those snippets of writing externally.
I don't pretend to be very computer-savvy or "techie"--just the opposite. That is why I take such threats as this new-on-the-scene virus seriously. I don't like having to pay for costly computer repairs, and I especially don't want to chance losing any files I consider important.
Hopefully, the good guys (and gals) will catch the bad ones--the hacker/extortionists--and put an end to CryptoLocker for good!
CryptoLocker Info Guide
Thanks for reading and supporting this HubPages writer!
Please vote and leave comments. Your feedback is valuable--especially if you're one of the many HubPages members or visitors who IS computer-savvy and/or "techie" and may be able to offer some useful protective advice for the rest of us.
NOTE: I am the author of this article, and it is owned by me in entirety. It is not available for use by reproducing in any form without my express written permission. If you see all or any part of this article (as written) on another site, please notify me where it can be found. Theft of a writer's work is plagiarism, and stealing another's words is no less wrong than any other theft.
Good Portable Hard Drive
© 2013 Jaye Denman